“Is this a bug?” is a question we are often asked.
Usually the answer is, “I understand why you are asking is this a bug. Some bugs do look similar to this. But, here is what you actually found.”
Real electronic eavesdropping devices are getting smaller. So are lots of other little electronic bits which are part of our everyday lives. Distinguishing between the two can be tricky. If the object you found makes you think, is this a bug, keep reading. You stand a good chance of finding your answer here.
Many things people find fall into two categories; gadgets meant to annoy, or small electronic circuits which were once part of something else. By the time these are found the batteries are usually dead. This makes the object even more mysterious since it is not obvious as to what the thing does.
The Annoy-A-Tron Family
These comprise most of our is this a bug inquiries, so let’s have a look at them to see if this is what you found.
Annoy-A-Trons are prank electronic devices which emit sounds (buzz, chirp, beep, whistle, etc.) at random intervals. The often have magnets to make them easy to hide (under desks, behind cabinets, in light fixtures, etc.). The batteries can last up to three years. And, of course, they are meant to be annoying.
While active, these devices are distracting, and can be really hard to find. But, eventually they loose power and people forget they were ever there.
Annoy-A-Tron type devices are usually found when furniture is moved, during renovations, or while retrieving something that has dropped under or behind a desk. They are also discovered in workplaces during TSCM inspections. Because these devices are hidden, look spooky, and don’t seem to have a purpose, people naturally tend to think someone has bugged them.
Should you find one, replace the battery, and extract your revenge.
A close cousin to the Annoy-A-Tron is the recordable sound prank. The difference with these devices is you can record your own sounds, like: “I’m watching you,” screams, burps, farts… well, you get the idea.
Some custom sound makers are embedded into things like greeting cards and children’s toys. Once removed from their original packaging they can definitely make you think you found a bug. These photos will help you determine if your is this a bug is one of these.
Toys that make you think, “Is this a bug?”
Electronic circuits which become separated from toys and clothing can look suspiciously like electronic surveillance devices; easily misidentified as audio eavesdropping bugs, or GPS trackers, for example. Here are the types of things we have been asked to identify over the years.

Is This a Bug: Case History 1
All we received was this photo…

Not much to go on. It was obviously a sound generator. The speaker is on the right. The center piece looks like a pushbutton. And, the brains and batteries are on the left. With the help of a colleague, its origin was finally puzzled out.
In 1993, Turner Home Entertainment released the 60th anniversary, VHS, colorized version of RKO’s King Kong. The presentation box had this sound device secreted between the cardboard layers. It allowed one to hear King Kong roar when his chest was pressed! We are guessing that when the batteries died some inquisitive person did an autopsy on Kong and extracted the device. The rest is history.
Is My Hotel or Airbnb Bed Bugged?
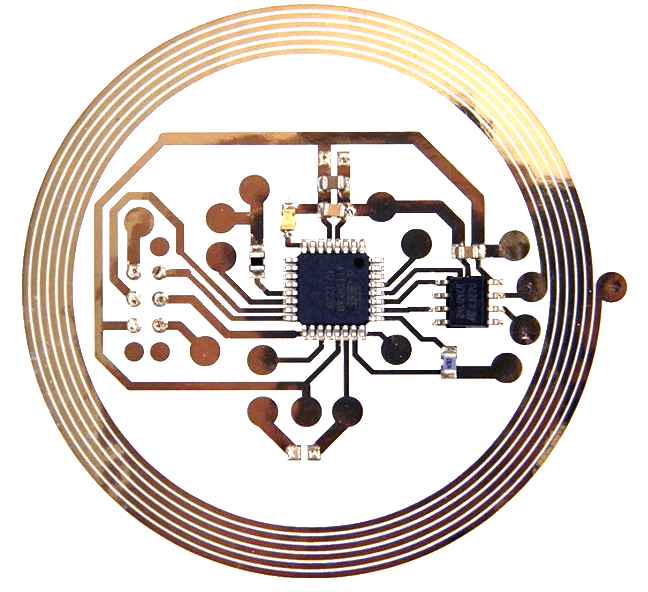
We get asked this when someone finds a bit of miniature electronics embedded in the sheets or other linens.
If you are seeing one of these buried in the hem of your linens the answer is, No. You can relax.
These are RFID tags. Commercial laundries attach them to linens to keep track of who belongs to what.
As one supplier explains…
“UHF RFID textile laundry tags are designed to optimize industries laundry processes, providing durability and suitability for washing, drying, dry cleaning and ironing. They can be used for many different applications such as laundry application, logistics, anti-counterfeiting, supply chain management control, inventory control, asset tracking, process control…”
Still concerned about privacy in your rented bedroom? Check here to learn how to find hidden spy cameras.
Is This a Bug: Case History 2
The most amusing identification request we have received so far involved this guy…
An employee at one of our client’s locations turned this into the security director. The employee was convinced, due to other events in her life, it was a bug. We examined it, replaced the batteries, and turned it on. The video results of our inspection appear here. It was obvious at the outset that this was not an electronic listening device… but it was a bug, a toy bug.
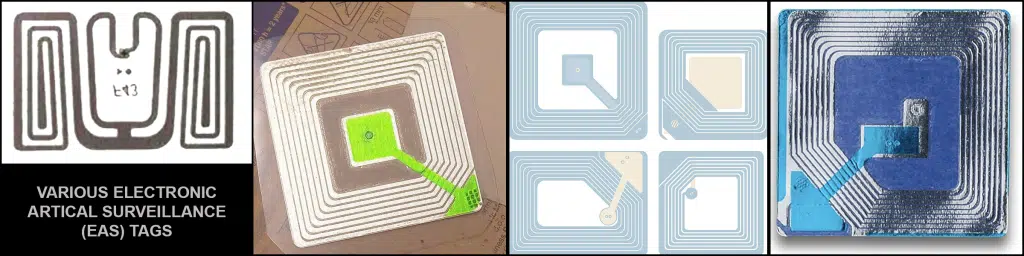
Electronic Article Surveillance (EAS) & Near Field Communications (NFC) Devices
These two groups of devices appear similar, but operate a bit differently. EAS tags are mostly associated with anti-shoplifting. NFC devices are associated with touch-less smartphone payments at credit card terminals, and general information transfer. They can look similar to one another, and like bugs, due to their spiral antennas.
Is This a Bug: Case History 3
One of our clients sent his suit to the dry cleaners. Upon its return he noticed the bottom right side of the jacket felt a bit stiff. He knew his competitors and the media were interested in where he goes and with whom he meets. Having good security awareness, he suspected a tracking device had been placed in the jacket lining. Our investigation revealed he had left his card-key in the pocket before sending it off to the cleaners. The dry cleaning chemical solvents, and subsequent steam pressing, had melted the card-key into the material. Case closed.
If you came to this page looking for an answer to your—is this a bug—question, we hope you found an answer. If an answer wasn’t found, maybe you did find a bug. Time to read, “I think I found a bug. What should I do?”
In the business world, executives don’t wait for someone to accidentally find a bug. Quarterly, pro-active inspections are the norm. Contact us for no-obligation advice on how to add Technical Surveillance Countermeasures (TSCM) to you security program.
Kevin D. Murray CPP, CISM, CFE, CDPSE is a business counterespionage consultant and TSCM specialist with over four decades of experience.
Murray Associates is an independent security consulting firm, providing eavesdropping detection and counterespionage services to business, government and at-risk individuals.
Headquartered in the New York metropolitan area, a Murray Associates team can assist you quickly, anywhere in the United States, and internationally.